Have you ever considered the most secure method to store your cryptocurrency? A hardware wallet provides an essential safeguard solution for your cryptocurrency assets by keeping them offline. Unlike hot wallets, which can be susceptible to cyber-attacks, hardware wallets securely contain the private keys you need to gain access to your digital assets.
Some hardware wallets are as small as a thumb drive. They can be connected to your computer or smartphone for transactions or balance reviews.
Built with reinforced security, these wallets adopt robust encryption to resist potential hacking attempts and malicious software. They're even fortified against physical harm and provide easy backup and recovery options if misplaced or stolen. The decision on the appropriate hardware wallet is crucial.
Read on for guidance in finding the right hardware wallet for you.
TL;DR
A hardware wallet securely stores private keys for cryptocurrencies, protecting against online threats.
These wallets store private keys offline on a secure physical device to prevent hacking and malware.
Interacting with a hardware wallet is necessary to complete transactions, which adds extra protection and significantly reduces the risk of remote hacking.
Cryptocurrency storage devices provide secure storage with PIN protection and backup seed phrases.
Hardware wallets are more secure than hot wallets because they're stored offline, but they may be less convenient for frequent transactions.
What's a hardware wallet?
A hardware wallet is a physical device designed to store and manage private keys for cryptocurrencies like Bitcoin securely. Unlike software wallets on computers or smartphones, hardware wallets are isolated, dedicated devices. They provide an extra layer of security against online threats such as hacking, malware, and phishing attacks.
How hardware wallets work
Generating and storing private keys
When you set up a hardware wallet, it generates a random set of cryptographic keys, including a private and corresponding public key. The private key is a long, unique, and secret alphanumeric string that allows you to sign transactions and control access to your funds on the blockchain. The private key is crucial and must be kept secure at all costs.
Secure element
Most hardware wallets use a secure element, a tamper-resistant chip that stores the private keys and performs cryptographic operations. This secure element makes sure the private keys remain inaccessible and safe from external threats.
Offline operation
Hardware wallets operate offline, meaning they're not directly connected to the internet during normal use. This isolation reduces the chances of unauthorized access and prevents potential attacks from online threats.
Transaction signing
When you want to make a cryptocurrency transaction, the hardware wallet connects to a computer or a mobile device. The transaction details are sent to the hardware wallet, securely signed with the private key. The signed transaction is then sent back to the computer or device for broadcasting to the blockchain network.
The importance of private keys
Private keys are the backbone of cryptocurrency security. They provide the necessary proof that you are the rightful owner of the funds stored on the blockchain. Owning the private key associated with a particular cryptocurrency address means controlling the funds linked to that address. Losing the private key could result in permanent loss of access to those funds, as there's no central authority to retrieve them.
Example: using a hardware wallet to keep Bitcoin safe
Let's say you want to store your Bitcoin securely using a hardware wallet.
Purchase a hardware wallet
Choose a reputable hardware wallet from well-known manufacturers like Ledger, Trezor, or KeepKey. Purchase the device from an authorized retailer to make sure it hasn't been tampered with.
Set up the hardware wallet
Follow the manufacturer's instructions to set up the hardware wallet. During this process, the device will generate a new private key that only you'll know.
Backup the recovery seed
Hardware wallets often generate a recovery seed — a list of words that can be used to restore access to the wallet in case the device is lost or damaged. It's essential to write down this seed on a piece of paper, and keep it in a safe and separate location from the hardware wallet itself.
Transfer Bitcoin to the hardware wallet
Send your Bitcoin from your exchange or software wallet to the public address provided by your hardware wallet. This way, the Bitcoin is securely stored in the hardware wallet's address, protected by the private key residing on the device.
Secure storage
Store your hardware wallet in a safe place, such as a fireproof safe or a secure location only known to you. Keep it away from potential hazards like water or extreme temperatures.
Transaction signing
When you want to spend or transfer your Bitcoin, connect the hardware wallet to a computer or mobile device, authorize the transaction on the hardware wallet using your private key, and then broadcast the signed transaction to the Bitcoin network.
By using a hardware wallet and following these steps, you can significantly reduce the risk of your Bitcoin being compromised by hackers or malware, making sure that your funds remain safe and under your control.
Remember, the security of your hardware wallet is only as strong as your protection of the private key and recovery seed. Always prioritize their safety and avoid sharing them with anyone.
Why are hardware wallets important?
With hardware wallets playing a pivotal role in the secure storage of cryptocurrencies, they have several security advantages over other types of wallets. Let's explore them.
Offline storage
Hardware wallets store private keys offline in "cold storage," protecting them from online threats such as hacking or malware.
Physical security
Many hardware wallets require physical interaction, like pressing a button, to confirm transactions. This makes remote hacking nearly impossible.
Immunity to computer vulnerabilities
Your private keys remain secure within the hardware wallet even if your computer is infected with malware or compromised.
PIN protection
Hardware wallets often have PIN protection, adding an additional layer of security to prevent unauthorized access.
Recovery options
If a hardware wallet is lost or stolen, assets can be recovered using a backup seed phrase, which is typically a 12 to 24-word sentence created during the wallet setup.
Encrypted private keys
The private keys stored in the hardware wallet are often encrypted, providing an extra layer of security.
Limited attack surface
These wallets are typically simple devices with the sole function of storing and signing transactions. However, they have a limited attack surface compared to software wallets or exchanges.
Cold vs. hot wallets
"Cold storage" refers to an offline mode of storing these digital assets. It's essentially the practice of keeping a reserve of cryptocurrencies in a place that's not connected to the internet, such as in a hardware or paper wallet.
The primary purpose of this practice is to protect these assets from cyber threats, such as theft and hacking. This makes cold storage one of the safest ways to store cryptocurrencies as it greatly reduces the risk of digital attacks that are often associated with internet-connected storage options.
A "hot wallet" is a digital wallet connected to the internet. These wallets provide greater convenience for frequent trading and transactions. However, their internet-connected nature makes them more susceptible to hacking attempts and other online vulnerabilities.
Opting for cold storage methods is generally recommended if you hold a substantial amount of cryptocurrencies and don't need to access them frequently. This way, you can guarantee better security and peace of mind for your digital assets.
What's the difference between hot wallets and hardware wallets?
Let's review the difference between a hot wallet and a hardware wallet, which basically boils down to an internet connection. Depending on the type of wallet you're looking for, they both provide a valuable purpose. However, you should also be aware of their limitations.
Hot wallets
A hot wallet is a digital wallet connected to the internet. These wallets provide greater convenience for frequent trading and transactions of digital assets.
Pros:
Easy to use and manage
Convenient for regular transactions, providing quick access to funds
Often free and support multiple types of cryptocurrencies
Integrated features such as direct trading on crypto exchanges
Cons:
Vulnerable to online threats, including hacking and phishing.
Dependency on third-party services that can be compromised or go out of business.
Not ideal for storing large amounts of cryptocurrency due to security risks.
Cold wallets
A cold wallet keeps private keys disconnected from the internet, providing enhanced security against online threats and hacks.
Pros:
Provides the highest level of security among wallet types, keeping private keys offline
Immune to online threats and attacks
Ideal for storing large amounts of cryptocurrency for the long term
Cons:
Less convenient for frequent transactions as it requires physical access to the device
Usually not free, with the cost depending on the brand and features
The risk of loss or damage to the physical device could lead to the loss of assets if not correctly backed up
It can be less user-friendly than hot wallets, especially for beginners in cryptocurrency
What are the best hardware wallets for 2024?
Keystone Wallet
Keystone is a QR-code hardware wallet isolated from the internet, which helps reduce the opportunities for errors. Keystone is compatible with MetaMask (Extension and Mobile), OKX (Extension and Mobile), and other leading software wallets like Solflare, Sender, Fewcha, and more.
It supports BTC and other EVM-compatible chains, as well as non-evm chains such as Cosmos, Aptos, Near, Sui, Polkadot, etc. Keystone Wallet has a 4-inch touch screen, open-source product code, and support for PSBT multi-signature, which makes it easy to use and protects digital assets. Using a cold-end (hardware wallet) and a hot-end (smartphone) dramatically simplifies the operation process while protecting the security of digital assets.
It may be expensive for new traders, and because of its dedicated community base, it often sells out and isn't always accessible
Tangem
What if your wallet was as thin as a credit card? If that sparked your curiousity, Tangem may be the wallet for you. It features a chip developed alongside Samsung Semiconductor — a subsidiary of the manufacturing conglomerate — and provides robust security and durability. A chip embedded in the card generates a random private key that's never revealed. Meanwhile, biometric security and access code protection are further security-focused features.
The Tangem wallet is easy to set up, and requires you to simply tap the card on your phone. One Tangem wallet set includes up to three identical Tangem cards — similar to copies of your house key. The cards connect securely with each other and transfer your encrypted private keys.
The wallet offers you access to thousands of digital assets, and also integrates with the OKX Wallet for crypto swaps. The Swiss-based company is currently working on a hardware wallet ring, too.
Ledger Nano X
The Ledger Nano X boasts Bluetooth, USB-C capabilities, and a rechargeable battery. It supports 1,800 digital assets, and can store up to 100 applications, including Bitcoin and Ethereum. The Nano X's Bluetooth is only compatible with the mobile app, not desktop.
Despite common misconceptions, the Ledger Nano X doesn't provide better security than the Nano S. Both hardware wallets use the same security chip, require a PIN code for access, and provide a 24-word recovery phrase for backup. The main difference lies in the Ledger Nano X's added Bluetooth functionality and expanded application storage capacity, setting it apart from the Nano S.
One of the drawbacks is that Nano X doesn't offer a touch screen, which some users would prefer. Meanwhile, the device's Ledger Recover feature has raised some concerns. Ledger Recover is designed to enhance private key recovery, but it involves sharding private keys to centralized entities. Questions were raised about potential security risks and backdoors, which could impact user trust in Ledger’s operational practices. What's more, new users may find the setup and usage challenging, requiring time and effort to understand features, security protocols, and proper use.
Ledger asserts that its hardware wallets stand out because they uniquely combine a Secure Element with a custom OS. This innovative framework effectively isolates crypto apps, significantly mitigating the risk of cyber attacks.
Trezor Model T
Developed by SatoshiLabs, the Trezor Model T is an ideal hardware wallet for beginners. Its straightforward setup, intuitive touchscreen, and user-friendly interface make it easy to use. The Trezor Wallet application lets you purchase and exchange assets and tokens directly, enhancing your crypto management experience. The device offers native support for 14 assets, including Bitcoin, Ethereum, and Dogecoin. The Model T also extends compatibility to over 8,000+ altcoins and tokens.
The Trezor Model T prioritizes security by storing your private keys offline within the device, reducing the risk of compromise. A PIN code is required to access the hardware wallet, and any changes or transactions must be physically confirmed using the buttons on the device.
The Trezor Model T also offers an additional security layer, allowing you to create a passphrase. This feature makes a separate account on the wallet where you can store specific assets. Even if someone gains access to your PIN, the assets stored under the passphrase-protected account remain secure and inaccessible. Meanwhile, Trezor’s backup system sets the standard in case of a lost device. The 12-word Standard Backup serves as a fail-safe for asset recovery, while the Shamir Backup, with split recovery seeds comprising 20 words, adds an extra layer of protection. This method allows users to recover their wallet using word combinations.
It's important to note that the wallet doesn't work for iOS users and is only supported on the OKX wallet web browser extension. Additionally, while the Trezor Suite allows for coin management, including purchases and swaps, it lacks native support for NFT management or staking. What's more, the price falls on the expensive side when compared to other hardware wallets.
D'CENT Biometric Wallet
The D’CENT Biometric Wallet is a new way to manage cryptocurrency safely. It uses biometric authentication to protect your digital assets better and costs less than other wallets at $89.
With its fingerprint sensor, the wallet provides an extra layer of security, making it difficult for hackers to gain access. It also offers a seamless connection with DApps, allowing you to explore different blockchain ecosystems. Its large OLED display and user interface appeal to the community, especially when it comes to keeping their assets safe without compromising convenience with complex steps.
Besides its biometric features, the wallet provides offline storage, keeping users’ private keys separated from the internet to help minimize the risk of cyberattacks. For greater convenience, the D’CENT mobile app also syncs with the wallet, enabling users to manage their assets, track balances, and perform transactions on the go.
This combination of security and ease of use has made the D’CENT Biometric Wallet a preferred choice for beginners and crypto veterans. For those who prefer a more compact option, D’CENT also offers a Card Wallet. This thin, NFC-enabled card lets you store and manage digital assets with the same high level of security in a portable form.
Ellipal Titan
The Ellipal Titan is an air-gapped cold storage wallet constructed with a metal seal, enhancing its resistance against tampering. Its data transmission relies on QR code scanning, eliminating the need for connection interfaces like USB, Wi-Fi, or Bluetooth, which increases its security. Its operations are enabled by the Ellipal App, making transactions as simple as scanning a few QR codes.
In the event of a successful breach into its physical casing, the device is designed to erase all the saved private keys. Despite this, your assets remain secure and can be retrieved using the recovery seed generated during the device's initial setup.
The Ellipal Titan is a mobile-focused hardware wallet, so there's no desktop support. It can hold over 10,000 digital assets, and the team steadily adds new ones weekly.
SecuX V20
The SecuX V20 is a cryptocurrency wallet well suited for individuals requiring management of multiple accounts who prioritize high security. Additionally, its Bluetooth functionality and color touch screen may appeal to tech-savvy users. Despite its features, the SecuX V20 boasts an intuitive interface, allowing even first-time hardware wallet users to get started within minutes.
The Hidden Wallet feature of the SecuX V20 offers a secure and private way to partition your funds. You can establish a hidden wallet in the app that's separate from your main account, adding an extra layer of security and providing more control over your funds. This functionality removes the need to invest in a secondary hardware wallet, offering cost savings and an extra layer of security.
Some users have flagged it tends to be heavier and bulkier than other wallets on the market.
NGRAVE ZERO
NGRAVE, similar to the Ellipal Titan, is another air-gapped hardware wallet. The term "air-gapped" signifies that the device can't establish network connections, isolating it from external cyber activities. This separation plays a crucial role in enhancing the wallet's security, as it creates an impenetrable wall that prevents remote hackers from breaching the device.
Stylistically, the NGRAVE ZERO looks similar to a premium mobile device. With its elegant black casing, it features a color touch screen, combining high-end technology with sophisticated design.
The NGRAVE ZERO device is the world's first hardware wallet to receive an EAL7 certification. This certification represents the pinnacle of security ratings within the blockchain and financial sectors. In the past, other hardware wallets had experienced security breaches when hackers managed to physically open the devices and use advanced tools to send electrical pulses that extracted data from the chips. In response, NGRAVE designed the ZERO to resist these threats, making its physical structure secure.
The product does fall within the premium price range, and there's no integration with DeFi protocols.
KeepKey
The KeepKey hardware wallet is a cost-effective and convenient solution for storing cryptocurrency, combining security and usability. With a price of $49, it stands out for its affordability, making it a top choice for users looking for a budget-friendly option without compromising quality.
The design of KeepKey includes a generous display and strong construction, with a back made of anodized aluminum and a polycarbonate covering, making it long-lasting.
Despite only supporting a small range of 40 cryptocurrencies, its user-friendly design and spacious screen make it a convenient option for storing popular coins and ERC-20 tokens. The device is larger than its rivals, such as Ledger Nano S and Trezor One.
How to choose the right hardware wallet
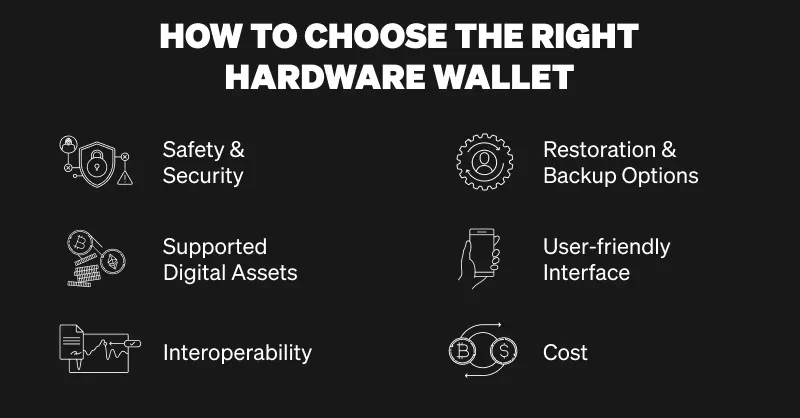
When it's time to buy your hardware wallet, here are some things you should consider and assess before purchasing.
Safety and security
When shopping for a hardware wallet, make sure it comes with comprehensive safety measures such as PIN codes, passphrase safeguards, is air-gapped, and includes biometric identification. It should also use state-of-the-art encryption to protect the device from hacking and cyber-attacks.
Supported digital assets
Check if the hardware wallet is compatible with the specific digital assets you plan to invest in. Since some wallets may restrict some cryptocurrencies, verifying this information beforehand is essential.
Interoperability
Choose hardware wallets that can integrate with other wallet interfaces. This feature is handy if you interact directly with decentralized finance platforms or NFT applications from the wallet.
Restoration and backup options
Confirm if the hardware wallet offers options for backup and recovery in the event of loss or damage. Carefully follow the manufacturer's guidelines to back up your private keys and seed phrases securely.
User-friendly interface
Opt for a hardware wallet that offers a straightforward and intuitive user interface. This ensures seamless navigation and smooth transaction processes. An overly complex interface could lead to mistakes that might compromise your cryptocurrencies.
Cost
The price of a hardware wallet should align with your budget and the features it provides. More expensive wallets generally offer superior features and security, but there are also cost-effective options with solid security. Consider the balance between cost and functionality that suits your needs best.
The final word
Hardware wallets provide an essential layer of security for your cryptocurrencies by storing your private keys offline, safe from cyber attacks. These compact devices connect to your computer or smartphone for transactions and balance checks, encrypting your information to protect against potential hacking attempts. They also offer physical resilience and include easy recovery options, should they be lost or stolen.
When considering a hardware wallet, assessing your personal needs and security is critical. Not all hardware wallets are created equal, and the right choice depends on your circumstances. Factors such as ease of use, cost, company reputation, and additional security features are all important considerations.
Always remember that the ultimate goal is to protect your cryptocurrencies most effectively. Invest some time in research and consider your needs to make sure you choose the most secure and convenient option for your digital assets.
FAQ
A hardware wallet is a physical device designed to securely store the private keys used to access cryptocurrencies. Unlike software wallets, which are connected to the internet and are therefore at risk of a breach, hardware wallets keep private keys offline. This gives them an extra layer of security against hacking and malware.
Hardware wallets make and store private keys using a secure element. This element is a chip that can’t be broken and keeps the keys safe from outside threats.
When you make a transaction, the hardware wallet signs it with the private key. The wallet then sends the signed transaction back to your connected device for sharing to the blockchain. This largely offline operation significantly reduces the risk of unauthorized access and cyber attacks.
Hot wallets are digital wallets connected to the internet, making them convenient for trading and transactions. However, they’re more susceptible to hacking and online attacks. Hardware wallets, meanwhile, store private keys offline, offering enhanced security by safeguarding against online threats. Hardware wallets are considered by many to be less convenient for regular transactions because they require physical access to the device.
When selecting a hardware wallet, first start by understanding your priorities from the device. Security should be high on the list if not top, but you might also prioritize usability or resilience. Once you understand your priorities, take the time to do your own research to find a device you're confident in. Attempting to use a device that's too complicated could compromise the security of your assets should you make a misstep. Some of the general key factors and features to look into include:
Pin codes
Passphrase safeguards
Biometric identification
Compatibility with your digital assets
Interoperability with other wallet interfaces
Backup and recovery options
User-friendly interface
Cost
Activele digitale, inclusiv criptomonedele stabile, presupun un grad ridicat de risc și pot fluctua foarte mult. Ar trebui să analizați cu atenție dacă tranzacționarea sau deținerea activelor digitale este potrivită pentru dvs. pe baza situației dvs. financiare și a toleranței dvs. la riscuri. OKX nu oferă recomandări pentru investiții sau active. Sunteți exclusiv responsabil pentru deciziile dvs. de investiții, iar compania OKX nu este responsabilă pentru nicio pierdere potențială. Performanța trecută nu indică rezultatele viitoare. Consultați un specialist în domeniul juridic/fiscal/al investițiilor dacă aveți întrebări despre circumstanțele dvs. specifice. Funcțiile OKX Web3, inclusiv OKX Web3 Wallet și OKX NFT Marketplace, sunt supuse unor termeni separați privind serviciile, pe care îi puteți accesa la www.okx.com.
© 2025 OKX. Acest articol poate fi reprodus sau distribuit în întregime sau pot fi folosite extrase ale acestui articol de maximum 100 de cuvinte, cu condiția ca respectiva utilizare să nu fie comercială. De asemenea, orice reproducere sau distribuire a întregului articol trebuie să menționeze în mod clar: „Acest articol are drepturi de autor atribuite OKX în anul 2025 și este utilizat cu permisiune.” Extrasele permise trebuie să menționeze numele articolului și trebuie să includă atribuirea, de exemplu „Numele articolului, [numele autorului, dacă este cazul], © 2025 OKX.” Nu este permisă nicio lucrare derivată sau alte utilizări ale acestui articol.